Difference between revisions of "Agilla"
| Line 12: | Line 12: | ||
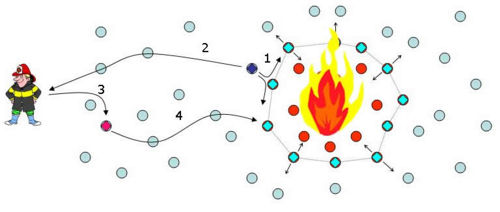
There are many applications of mobile agents in WSNs. Three of them include intruder detection, wildfire tracking, and cargo tracking. In intruder detection, detection agents are deployed around the perimeter of a WSN. When an intruder breaches a perimeter, the agents near the breach follow the intruder and clone themselves to form a perimeter around the intruder. Note that only the nodes next to the intruder are involved with tracking process. All other nodes are free to service other applications. In wildfire tracking, as shown in Figure 1, mobile agents swarm around a fire forming a perimeter, and dynamically adjusting it based on the movements of the fire. The algorithm for adjusting the perimeter is fully distributed, ensuring scalability. In cargo tracking, a multi-hop WSN is deployed on cargo containers. Each container has a mote that contains an electronic manifest. These motes go one step beyond RFID tags in that they can perform computation, such as monitoring sensors for intrusions or contract violations. When a ship docks, agents are deployed onto the ship's WSN. These agents scour the cargo containers identifying those that contain specific items or require inspection. Mobile agents are necessary in this case since the port authorities do not trust the code of other countries to return valid results. Also changing security levels and policies require a flexible software infrastructure, which is provided by mobile agents. | There are many applications of mobile agents in WSNs. Three of them include intruder detection, wildfire tracking, and cargo tracking. In intruder detection, detection agents are deployed around the perimeter of a WSN. When an intruder breaches a perimeter, the agents near the breach follow the intruder and clone themselves to form a perimeter around the intruder. Note that only the nodes next to the intruder are involved with tracking process. All other nodes are free to service other applications. In wildfire tracking, as shown in Figure 1, mobile agents swarm around a fire forming a perimeter, and dynamically adjusting it based on the movements of the fire. The algorithm for adjusting the perimeter is fully distributed, ensuring scalability. In cargo tracking, a multi-hop WSN is deployed on cargo containers. Each container has a mote that contains an electronic manifest. These motes go one step beyond RFID tags in that they can perform computation, such as monitoring sensors for intrusions or contract violations. When a ship docks, agents are deployed onto the ship's WSN. These agents scour the cargo containers identifying those that contain specific items or require inspection. Mobile agents are necessary in this case since the port authorities do not trust the code of other countries to return valid results. Also changing security levels and policies require a flexible software infrastructure, which is provided by mobile agents. | ||
| − | [[Image:FireDetection.jpg| | + | [[Image:FireDetection.jpg|left|thumb|500px|Figure 1: Wild fire tracking. (1) A fire detection agent detects fire and clones itself. The clone transforms itself into a fire tracking agent that repeatedly clones itself until a perimeter has been formed. Once formed, the agents continuously adjust the perimeter by migrating and cloning themselves. (2) A notification is sent to a fire fighter notifying him of the fire's location. (3) The fire fighter injects a guidance agent into the network that leads the fire fighter along a safe route to the fire.]] |
== Motivation == | == Motivation == | ||
Revision as of 22:08, 6 December 2007
A Mobile Agent Middleware for Wireless Sensor Networks
Download | Documentation | Examples | Publications | Related Work | Forum
Introduction
Agilla is a middleware that provides a mobile-agent paradigm for programming and using wireless sensor networks (WSNs) . Agilla applications consist of mobile agents that can proactively migrate their code and state across the network. Mobile agents offer more flexibility by allowing applications to control the way they spread. They can position themselves in the optimal locations for performing application-specific tasks. They can save energy by bringing computation to the data rather than requiring that the data be sent over unreliable wireless links. They can increase the utility of a WSN by constraining themselves to the specific locals that are relevant to their application's requirements (in contrast to spreading throughout an entire network), and sharing the resources of a single node, i.e., multiple mobile agents can reside on each WSN node. Other systems like Deluge and Maté allow in-network reprogramming. Agilla, however, goes one step further by allowing programs to control where they go and to maintain both their code and state across migrations.
Since new agents can be injected into a pre-existing network, the network can be re-tasked. Since each agent executes autonomously and multiple agents can simultaneously run on a node, multiple applications can co-exist. Since mobile agents can move and clone, they can quickly morph an application's installation base to handle unexpected changes in an environment. There are many other inherent advantages of using mobile agents, especially in a wireless sensor network. However, there are also many challenges, the foremost being the lack of computational resources and unreliable network connectivity. Agilla is the first mobile agent middleware for WSNs that is implemented entirely in TinyOS. It has been tested on Mica2 and MicaZ motes. It abstracts away complexities associated with developing WSN applications, and provides mechanisms that overcome the challenges associated with limited resources and unreliable network communication. It demonstrates the feasibility of using mobile agents within WSNs and, furthermore, it takes the first steps at identifying a minimal set of primitives that should be provided for facilitating highly flexible WSN applications.
There are many applications of mobile agents in WSNs. Three of them include intruder detection, wildfire tracking, and cargo tracking. In intruder detection, detection agents are deployed around the perimeter of a WSN. When an intruder breaches a perimeter, the agents near the breach follow the intruder and clone themselves to form a perimeter around the intruder. Note that only the nodes next to the intruder are involved with tracking process. All other nodes are free to service other applications. In wildfire tracking, as shown in Figure 1, mobile agents swarm around a fire forming a perimeter, and dynamically adjusting it based on the movements of the fire. The algorithm for adjusting the perimeter is fully distributed, ensuring scalability. In cargo tracking, a multi-hop WSN is deployed on cargo containers. Each container has a mote that contains an electronic manifest. These motes go one step beyond RFID tags in that they can perform computation, such as monitoring sensors for intrusions or contract violations. When a ship docks, agents are deployed onto the ship's WSN. These agents scour the cargo containers identifying those that contain specific items or require inspection. Mobile agents are necessary in this case since the port authorities do not trust the code of other countries to return valid results. Also changing security levels and policies require a flexible software infrastructure, which is provided by mobile agents.
Motivation
Most WSNs are inflexible application-specific systems; they are closed-systems that provide a limited set of services for a specific pre-determined set of users. As WSNs mature and motes become more sophisticated, large-scale WSNs consisting of thousands of nodes that span vast geographic areas will be deployed for longer periods of time. The large scale of these networks will inevitably lead to them being shared by multiple users, possibly simultaneously. These users are transient; they may come and go, sporadically using the network whenever and wherever they need to. The long deployment intervals ensure that the application requirements will change mid-deployment. The existing software infrastructure for WSNs does not provide the flexibility necessary for supporting these large-scale WSNs.
Presently, most WSNs are programmed prior to deployment and, once deployed, can only be tweaked through a static set of pre-defined parameters, severely limiting the WSNs flexibility. The network is limited to run a single application, which, as WSNs are deployed for longer intervals, becomes increasingly unacceptable. Also, the application itself may not be able to adapt to unpredictable changes in user requirements; it's simply not possible for software developers to foresee all possible uses of a WSN prior deployment. This is especially so as WSNs become larger, more sophisticated, deployed for longer periods of time, and over larger areas.